

Electronic signature for documents and requests in Bitrix24

What is an Electronic Signature for?
Sometimes documents need to be signed and sent, but the manager whose signature is required is on vacation. While waiting for him/her to return, it is possible to forget about them, or miss the deadline for sending them.
In cases where “missed deadlines” isn’t an issue, the manager is welcomed back to the office with piles of documents. This is how he spends the first few days back - signing documents.
“Paper” in the 21st century is a non-eco-friendly anachronism. It’s best to totally do away with them. But then, we still have to sign documents.
What is digital signature about?
Just the way a person places their signature with a pen on a physical document to show their agreement to the contents of the document, a digital signature is the same. The only difference is the paper and the signature do not exist physically.
Why do we need signatures? In a few words - for authentication (confirmation) of documents. That is, to prove that the signer agrees with the provisions of this particular version of the document.
Where can Electronic Signatures be applied in CRM systems and Company intranet portals
- Hey Steven, do you have a minute to sign these documents?
- Kristen, can you come back later, I’m busy now!
There are 2 scenarios for using an Electronic signature in a CRM:
-
For internal correspondence and document confirmation “with the push of a button”.
Internal documents, contracts and agreements are often coordinated in the interface of CRM systems and intranet portals. -
For external use - To send formal documents to clients, government agencies and other legal entities.
These scenarios differ in the requirements for each type of digital signature.
In the first case, we sign
-
Application for leave/ vacation
-
Applications for payments of various kinds
-
Other requests (for appliances, furniture, etc.)
-
Contracts, agreements, payment invoices.
The second usage scenario is more serious, and requires a legally binding or qualified electronic signature.
Technology: What is an Electronic signature? What types exist?

There are three types of Electronic signatures:
-
Simple Electronic signatures (SES)
-
Advanced Electronic Signatures (AES) -
There are two types
1. Qualified Electronic Signatures (QES)
2. Non-qualified Electronic Signatures (NES)
Simple Electronic signatures are the simplest type of e-signatures. eIDAS defines them as "data in electronic form which is attached to or logically associated with other data in electronic form and which is used by the signatory to sign." They do not require identity verification of the signer and “trust” in documents is the responsibility of the document receiver.
Unlike a simple signature, advanced and qualified electronic signatures require a verification of the signer. They also prevent the signer from modifying the contents of the document after their electronic signature has been placed on the document.
To generate any type of electronic signature, you need three things:
-
A Document
-
a public key
-
a private key
Let's analyze each type of electronic signature
Simple Electronic Signature
-
The system takes the document's metadata (document date, document number, title, signer's password, etc.) and hashes it. With this, the electronic signature is ready. The password is stored and generated by your system,
-
You send the file with your electronic signature,
-
The receiver gets the file
-
The user decrypts the signature using a password. The system compares the received metadata and login to see that they are correct.
A great example of a simple electronic signature in use is when we log into social networks (Facebook for example) with a username and password. To confirm your identity (sign a document), you need to enter your login and password (hash metadata).
The system checks if the user exists. If there is such a user, then password verification begins. If the password you entered matches the one in the system - congratulations, you have successfully logged into Facebook (metadata is compared after decryption).
One of the disadvantages of simple signatures is that if your password is somehow stolen, then the thief can go to your facebook page and do whatever they want. It’s the same with a document.
Advanced Electronic Signature
An advanced electronic signature protects against document modification. That is, if you make changes to the document after signing it, then the electronic signature automatically becomes invalid.

To generate signatures, certificates are used (like SSL, based on the same technology). The certificate has a limited validity period.
An Advanced Electronic signature can be either unqualified or qualified. The difference is what regulations the signature adheres to as outlined by the electronic Identification, Authentication, and Trust Services regulation (eIDAS regulation).
For a qualified Electronic signature, eIDAS regulation requires a qualified certificate stored on a qualified signature creation device and must be issued and managed by a QTSP (Qualified Trust Service Provider)
If a self-signed certificate is used or issued by an unaccredited CA (Certifying Authority), then such a signature is unqualified.
How Advanced Electronic Signature works
Recall the example of a simple signature algorithm. The result of this algorithm does not depend on the document text. If you submit this text to the input of the hash function, you get something similar to an advanced signature. That is, as a result of changing the text of the document, the old signature "does not match" with the new version of the document.
In reality, an advanced signature is a hash of a document encrypted with the private key of the certificate.
All participants in the workflow have a public key. It is used to verify the authenticity of the signature. The Private key is stored by the user and used to generate a signature.
What does an Advanced Electronic Signature look like?
Technically speaking, an advanced signature is a separate file (remember, in the case of a simple signature, it was a line). That is, in order to transfer the signed document to the other party, you need to transfer the source file and the signature file. However, some document formats allow digital signatures to be embedded.
For example, PDF and almost all Microsoft Office document formats allow advanced electronic signatures to be embedded in them. The software packages themselves have the function of creating and verifying such signatures. Thus, for the end users, the signing process looks like clicking a few buttons in Word, Excel, or Adobe Reader.

Non-qualified Electronic Signature (NES)
Non-qualified electronic signatures have legal power to some extent. Documents signed with Non-qualified E-signatures are legally binding. However, they cannot be used to sign documents from government agencies in some countries.
Users receive a certificate with a public and private key in a format and through a means that the parties trust. For example, in the form of a file sent via email.
Any software that the parties trust can be used to create the signature - OpenSSL, CryptoARM, or the built-in signing tools of Microsoft Office or Adobe Reader.
Qualified Electronic Signature (QES)
Qualified electronic signatures are legally binding and are recognized by the state i.e, they can be used for signing documents from government agencies. For example, you can send documents to the tax office. There is no need to conclude any additional agreements with the participants in the document flow - everyone trusts qualified electronic signatures“by default”.
The secret key for such a signature is transferred to the user on a secure medium (a USB token/flash drive, smart card, etc) issued by a QTSP (Qualified Trust Service Provider).

You need special software to work with the medium where the secret key is saved. Most often, this software integrates with the Operating System so that Microsoft Office, Adobe Reader, and other software packages can use the medium to create signatures.
For end users, the process of signing documents is simple - you only need to remember to connect a flash drive.
Using this type of signature, you can interact with government systems, participate in auctions, work with clients and partners.
Let's see two usage scenarios
Approval of internal documents
Usually, the procedure for issuing Leave applications, memos, reports, travel arrangements, etc resembles a quest. You need to find a form, fill it out, personally hand it over to the approver, etc.

If you are all in the same office, then such processes could take half an hour. But if production is in one location, and the personnel department is in another, it could drag on for days. The solution is the introduction of a document management system. We even have a separate workflow module.
One disadvantage - sometimes employees do not take “electronic documents” seriously enough. You can fix this with the introduction of an electronic signature. An unqualified electronic signature is a perfect solution to use.
In this scenario, there are 2 possible use cases:
-
to sign a document by uploading it in a special format on a separate page of the company’s intranet
-
Automatic approval and signing a document as it goes through a business process
Approval of External documents
For external document management, a qualified electronic signature must be used. This is the only way the documents will have full legal force. You will be able to exchange them with clients, partners and government agencies.
From the point of view of interfaces, everything looks like an internal workflow - a separate form for approval or automatic confirmation as part of a business process.
An important point - you need to pay more attention to security. Since we are talking about documents that have full legal force. Security is provided by access restriction, logging and separate notifications.
A simple example of using a signature in the CRM is to sign a contract document in a deal. After signing, you can send it to the client. There is no need to send documents by mail, wait several days or even weeks (if the client is in another city or country), and then wait the same amount of time for it to be returned. Instead, the document is authenticated by an electronic signature and is considered legally binding.
The main technical question remains - how can an Electronic Signature be implemented in the logic of a CRM or an intranet portal?
How to implement an Electronic Signature in a CRM
There are several solutions for working with E-signatures. Let's take a look at them.
One E-signature key for all employees
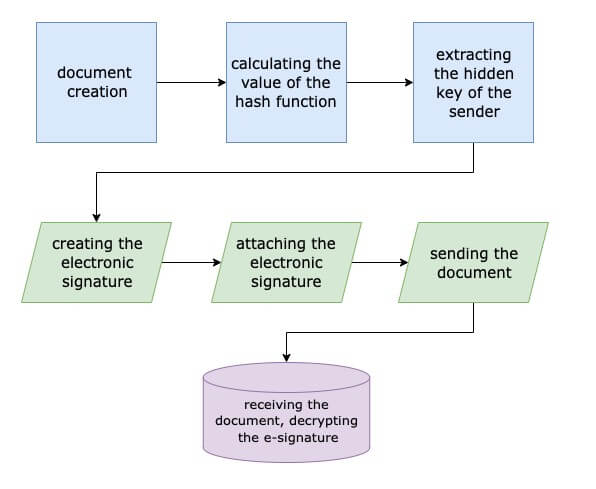
Suppose you need to sign a document and send it to a server. The server has to check the document and send a response, in the form of the same signed document.
And in both situations, a verification of the authenticity of the signature must be carried out. Suppose you have only one key for signing, there are lots of employees and each of them needs to sign and send documents. And this whole process needs to be done in the CRM.
How it works:
-
We create a separate server for electronic signature with a connected key, to which XML requests will come
-
Each employee who needs to sign a document will have to install a two-factor authentication application that will generate a one-time password every N seconds. (a TOTP). In turn, the server where the e-signature is located generates a QR code that needs to be scanned by this application in order for the password to appear. This password must be entered each time a signature is needed to confirm access to the USB key.
-
After signing, the request is sent to the server.
-
When the response is received on the E-Signature server in an XML format, it is then converted into a PDF file or any other needed format.
-
The PDF file is uploaded to the CRM.
This method is suitable for remote work, since all the employee needs is a smartphone. There’s no need to issue an E-signature token for each employee, one is enough for everyone.
This solution assumes that you completely trust the employees who have access to the interface. Even new company recruits sign documents using this method, as long as they have access.
This is a bad solution if signing documents have legal implications.
One E-signature key per Employee
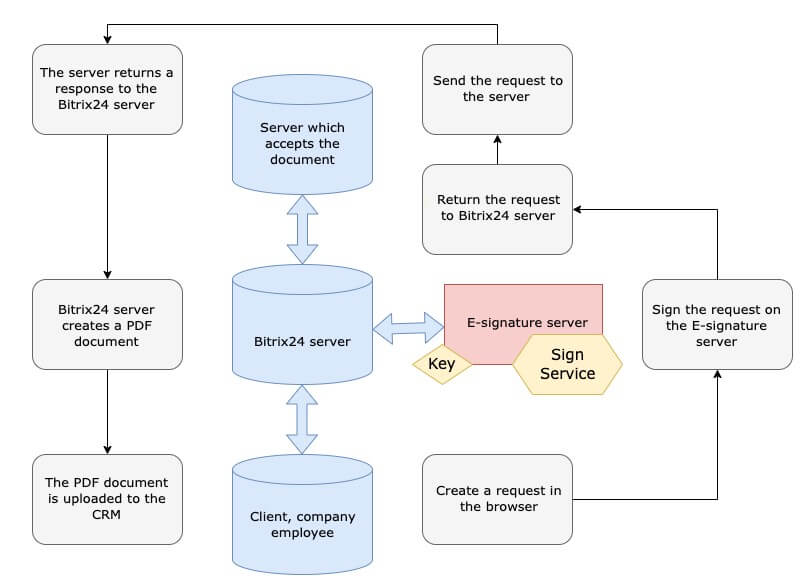
Suppose each employee who has privileges to sign documents has a key for an E-signature.
How it works:
-
We develop an application for workstations that will work with a crypto provider
-
An employee creates and signs a request at his workstation
-
The request is sent to the server.
-
The received response is converted to PDF or any other required file format
-
the PDF file is uploaded to the CRM
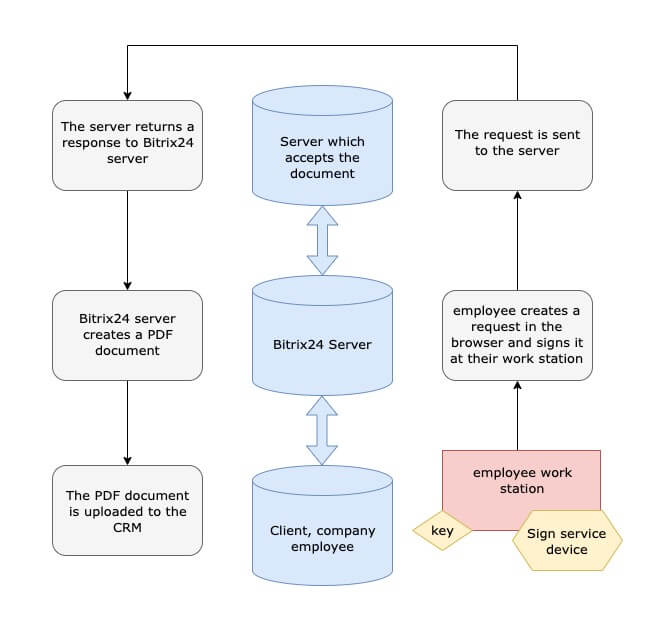
With this, we increase security, because only trusted employees can sign documents, and we know who signed what request.
How E-signature works in practice in a CRM
CEDIS, the national electricity distribution company of Montenegro contacted us to develop an E-signature solution. The business task was for employees to sign documents and send them to customers.

One server, one E-Signature key, CRM.
The task
Add a document in PDF format to a deal, sign it directly from the deal card using an E-Signature. The signed document can be downloaded and sent to the client.
How it was implemented
An additional field was created in the CRM, where the PDF document is uploaded. When a document is uploaded, the “Sign” button appears beside it. When you click on the button, the application interface opens.
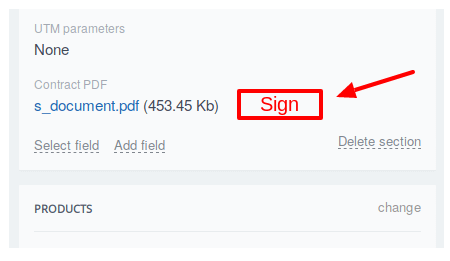
In order to sign a document, the user has to enter a one-time password which was sent to his smartphone and select a certificate with which to sign the document.
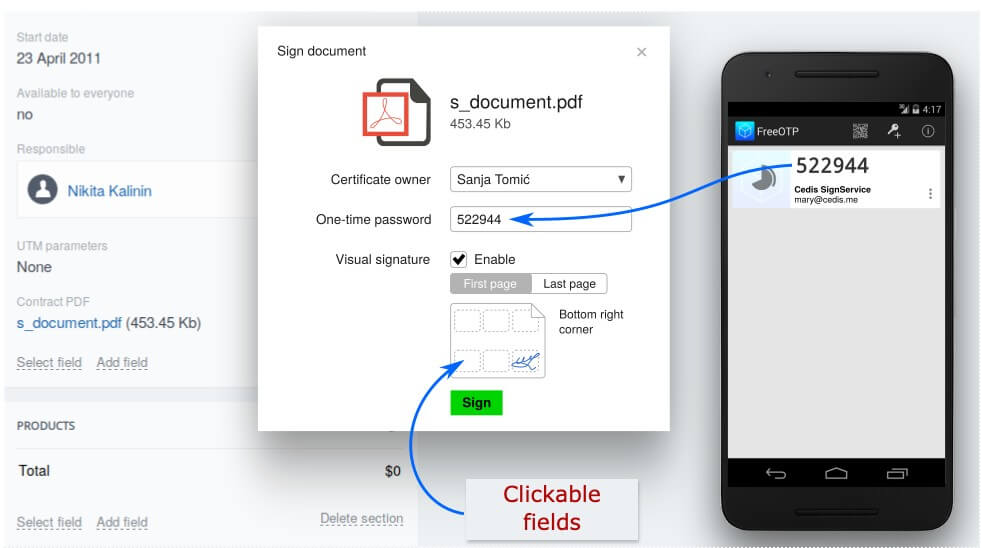
The document is sent to the server. The one-time password is entered and the certificate is selected. The document is signed and sent back. At this point, the unsigned document which was uploaded into the deal is replaced with a signed document from the server.
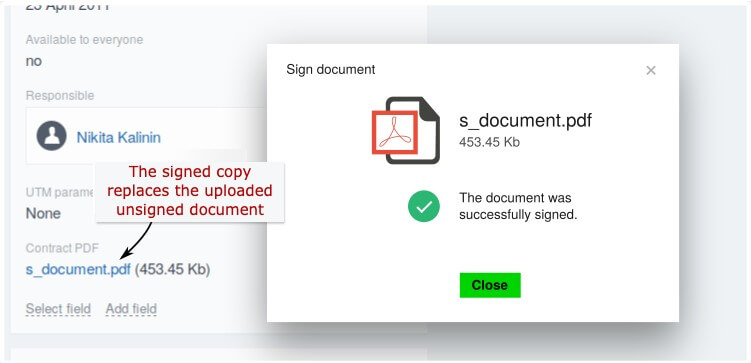
Now each employee who works with deals can sign a document using an E-Signature and send it to the client. There is no need to look for managers whose signatures you need. The manager also doesn’t have to worry about signing piles of paper.
This development cost about 200 developer hours. This includes the development of an application for the server, the development of an interface for Bitrix24, configurations and testing.
We have summarized our experience and offer the integration as a rental application.
Conclusion
At the moment, there are neither standard E-signature integrations nor specially developed modules for Bitrix24. If you need it, it can be done.
We possess the competence to do complex integrations and implementations. Write to us - we will analyze and estimate your task.
We can develop an E-signature solution according to your requirements.
The cost is from $3,500.
Send us a request.
- 13.09.2022
-
Nikita Kalinin
-
Demyan Seleznev
